Setup proxy in android is a vital talent for any Android developer or person. Understanding methods to configure a proxy server unlocks a world of prospects, from accessing restricted content material to boosting community efficiency and enhancing safety. This information offers a complete walkthrough, masking all the pieces from the fundamentals of proxy servers to superior configurations and troubleshooting widespread points.
This information will illuminate the pathway to mastery in dealing with proxy servers in your Android gadgets. We’ll delve into numerous strategies for configuring proxies, from simple system settings to extra complicated eventualities. Get able to navigate the digital panorama with confidence and ease.
Introduction to Proxies in Android
A proxy server acts as an middleman between your Android utility and the web. Consider it as a gatekeeper, filtering and doubtlessly modifying the info flowing to and out of your app. This middleman function permits for enhanced safety, improved efficiency, and larger management over community visitors. Understanding proxies is essential for growing strong and adaptable Android purposes.Proxies function by intercepting community requests out of your utility.
As a substitute of immediately connecting to a web site or server, your utility sends the request to the proxy server. The proxy server then forwards the request to the vacation spot and returns the response to your utility. This course of is clear to the person, offering a seamless expertise. Use circumstances embrace accessing restricted content material, bettering community efficiency by caching often accessed information, and enhancing safety by filtering doubtlessly dangerous content material.
Proxy Server Performance
Proxies provide important benefits in community eventualities, notably in enterprise environments. They allow corporations to regulate worker web entry, filter inappropriate content material, and improve community safety. For instance, a college would possibly use a proxy to dam entry to sure web sites whereas permitting entry to academic sources. Moreover, proxies can optimize community efficiency by caching often accessed content material, decreasing latency and bandwidth consumption.
That is particularly helpful for cell purposes the place bandwidth is a essential issue.
Forms of Proxies and Their Attributes
Several types of proxies cater to numerous wants. A standard sort is an internet proxy, particularly designed to deal with HTTP and HTTPS visitors. This sort is often used for internet looking and accessing web sites. One other class consists of SOCKS proxies, that are extra versatile, dealing with a broader vary of protocols. SOCKS proxies are recognized for his or her adaptability and might be configured for numerous duties.
Moreover, reverse proxies are used to enhance utility efficiency and safety. They sit in entrance of internet servers, appearing as a gateway for incoming requests.
Diagram of a Proxy Server Connection
Think about a simplified state of affairs. Your Android utility (represented by a smartphone icon) needs to entry a web site (represented by a globe icon). As a substitute of immediately connecting to the web site, the appliance sends the request to a proxy server (represented by a pc icon). The proxy server then forwards the request to the web site and receives the response. Lastly, the proxy server transmits the response again to the appliance.
This middleman step offers a managed and managed connection between your utility and the web. The connection is visualized as arrows connecting the smartphone, laptop, and globe, highlighting the movement of knowledge.
Strategies for Configuring Proxies: Setup Proxy In Android
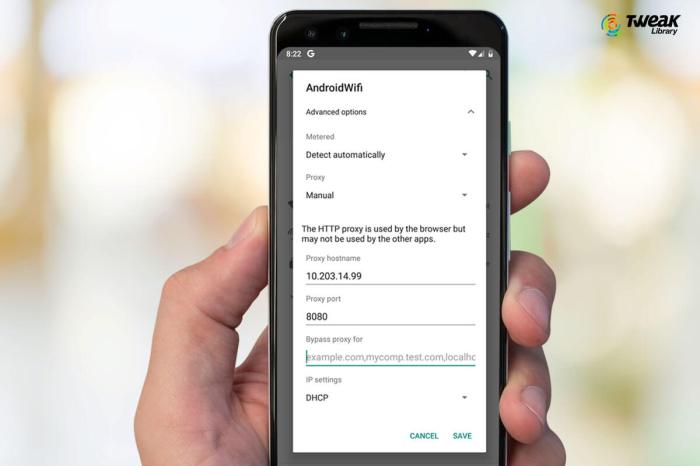
Unlocking the gateway to a wider web expertise usually requires configuring a proxy server. This significant step lets you route your web visitors by a chosen middleman, providing quite a lot of advantages, from enhanced safety to improved entry to content material. Understanding the varied strategies for configuring proxies in your Android system is vital to harnessing these benefits.Proxy configuration on Android is a simple course of, adaptable to your particular wants.
Totally different approaches cater to numerous preferences and technical proficiency ranges. Whether or not you like the intuitive graphical interface or a extra hands-on method, there is a methodology to fit your fashion.
Configuring Proxy Settings By Android System Settings
This methodology affords a user-friendly option to arrange proxy connections. It is notably helpful for individuals who desire a visible method to configuration.
- Navigate to Settings > Wi-Fi. Choose the Wi-Fi community you are related to and faucet on “Superior.”
- Search for the choice labeled “Proxy” or an identical designation. This selection is likely to be hidden inside a submenu. If you cannot discover it, examine for an choice labeled “Extra” or “Superior settings.”
- Enter the IP tackle and port variety of your proxy server. You will usually discover this info out of your proxy supplier.
- Choose the kind of proxy. Widespread varieties embrace HTTP and SOCKS. Select the suitable sort to your wants.
- Affirm the settings and save the configuration. Your system will now use the configured proxy server for all web visitors.
Configuring Proxy Settings By Wi-Fi Settings
Configuring proxy settings immediately by Wi-Fi settings affords a granular degree of management. This methodology is good for customers who require exact management over their proxy configuration.
- Open Wi-Fi settings.
- Choose the Wi-Fi community you are related to.
- Faucet on “Superior settings.” That is usually discovered inside a “Extra” or comparable choice.
- Find the “Proxy” choice, which is likely to be hidden inside a submenu.
- Enter the IP tackle and port variety of your proxy server.
- Choose the suitable proxy sort (HTTP, SOCKS, and so forth.) from the out there choices.
- Affirm the settings and save the configuration. Your system will now use the configured proxy server for all web visitors.
Evaluating Cell Information vs. Wi-Fi for Proxy Configuration
The tactic of proxy configuration does not inherently differ between cell information and Wi-Fi. The configuration course of is similar, whatever the community getting used. The important thing distinction lies within the community itself. Wi-Fi affords a extra steady and dependable connection, whereas cell information can fluctuate in high quality.
Totally different Forms of Proxy Configurations
Understanding the forms of proxies helps tailor your configuration to your particular wants.
- HTTP Proxies: These proxies work on the utility degree and primarily deal with HTTP visitors, comparable to internet looking.
- SOCKS Proxies: These proxies function at a decrease degree, dealing with numerous forms of community visitors, together with HTTP, FTP, and extra. They provide larger flexibility however require extra technical understanding.
Widespread Proxy Server Points and Troubleshooting

Navigating the digital panorama can generally really feel like navigating a maze, particularly when coping with proxy servers. Understanding the potential pitfalls and methods to overcome them is vital to seamless on-line experiences. This part dives into widespread proxy server points on Android, offering clear explanations and actionable options.
Widespread Proxy Configuration Errors
Correct proxy setup is essential for a clean on-line expertise. Incorrect configurations can result in numerous connectivity issues. Understanding the widespread errors and their cures is crucial.
- Incorrect Proxy Server Tackle or Port:
- Incorrect Proxy Authentication Credentials:
- Firewall or Community Restrictions:
Double-checking the proxy server’s IP tackle and port quantity is paramount. A typo or incorrect entry can fully block entry to the web. Be certain that the tackle and port are exactly matching the proxy server’s specs. Errors right here can vary from a easy typo to an incorrect port quantity, inflicting your system to fail to hook up with the proxy server.
Proxy servers usually require authentication. Inaccurate username or password particulars will stop connection. Confirm your credentials rigorously and guarantee capitalization matches the proxy’s necessities. This difficulty is commonly missed and might trigger frustration if not checked rigorously. Fastidiously evaluation the proxy’s authentication necessities and examine your credentials to them, verifying capitalization and any particular characters required.
Your Android system’s firewall or community settings is likely to be blocking the connection to the proxy server. Confirm that the proxy server’s port is open and allowed by your community safety settings. Guarantee your firewall settings aren’t blocking the mandatory ports. It is a widespread difficulty for customers with complicated community setups. Affirm the proxy server’s port is explicitly allowed in your firewall guidelines.
Troubleshooting Connection Failures
Connection failures can stem from numerous points, starting from easy typos to extra complicated community issues. Systematic troubleshooting is vital.
- Examine Community Connectivity:
- Confirm Proxy Server Availability:
- Clear Proxy Cache and Information:
A steady community connection is key. In case your system has poor community connectivity, the proxy server will not have the ability to join. Be certain that your web connection is energetic and functioning accurately. If the community is unstable, the proxy connection will doubtless fail. Check your web connection independently of the proxy to make sure it is steady.
Affirm the proxy server is operational and reachable. Check the proxy server’s accessibility utilizing an internet browser or different instruments to make sure it is functioning accurately. This may help rule out points with the proxy itself. If the proxy server is down, no quantity of configuration will assist.
Often, cached information can intervene with proxy connections. Clearing the proxy cache and information can resolve short-term glitches. Clearing cached information and cookies is a simple repair for transient issues.
Troubleshooting Timeouts and Different Community Issues
Sluggish speeds or timeouts might be irritating. A scientific method may help pinpoint the difficulty.
- Confirm Web Velocity and Bandwidth:
- Examine for Community Congestion:
- Disable Different Purposes Utilizing Community Assets:
Your web connection velocity and bandwidth can considerably have an effect on proxy efficiency. Examine your web connection velocity to find out if it is gradual or unstable. In case your web velocity is inadequate, the proxy will expertise efficiency points. Check your web velocity independently of the proxy to find out if the proxy is contributing to the slowness.
Excessive community congestion can influence proxy efficiency. Observe community visitors and search for potential congestion factors. If the community is overloaded, it may possibly result in gradual speeds and timeouts. Search for patterns in your community utilization and attempt to isolate when congestion happens.
Many purposes eat important community sources. Quickly disabling different network-intensive apps may help establish in the event that they’re contributing to the issue. If different purposes are utilizing an excessive amount of bandwidth, the proxy will doubtless expertise points. Examine if different purposes are utilizing important community sources and contemplate disabling them quickly to isolate the issue.
Widespread Proxy Errors and Options
This desk summarizes widespread proxy errors and their options:
| Error | Resolution |
|---|---|
| Connection Refused | Confirm proxy server tackle and port, examine community connectivity, and make sure the proxy server is energetic. |
| Timeout Error | Examine web velocity and bandwidth, search for community congestion, and disable different network-intensive purposes. |
| Authentication Failure | Confirm proxy authentication credentials, guaranteeing right username and password. |
| Proxy Server Unavailable | Examine proxy server standing, make sure the proxy server is operating, and is reachable. |
Sensible Purposes of Proxies in Android
Unlocking the complete potential of Android growth usually includes navigating complicated community landscapes. Proxies act as intermediaries, providing a variety of advantages for each builders and customers. They supply a layer of safety, optimize efficiency, and unlock entry to in any other case restricted content material. Understanding these purposes is vital to crafting strong and user-friendly Android purposes.Proxies should not only a theoretical idea; they’re highly effective instruments that may considerably improve the performance and reliability of your Android apps.
Think about a world the place you possibly can bypass geographical limitations, safeguard person information, and enhance the velocity of utility loading – that is the facility of proxies.
Use Circumstances for Setting Up a Proxy in Android Improvement
Proxies are versatile instruments, essential for numerous eventualities in Android growth. They aren’t only for large-scale enterprise purposes; they will enhance the safety and efficiency of any Android app.
- Community Safety and Privateness: Proxies can act as a vital protect, safeguarding delicate information throughout transmission. By routing visitors by a safe proxy server, Android apps can encrypt communications, making them much less susceptible to eavesdropping and malicious assaults. Consider it as a digital wall defending your app’s information from prying eyes.
- Accessing Restricted Content material: Geographical restrictions or content material filtering might be circumvented utilizing proxies. A proxy server positioned in a special area can masks the person’s location, granting entry to content material unavailable within the person’s fast space. That is notably helpful for builders creating apps with international attain, enabling customers to entry content material regardless of their location.
- Community Efficiency Optimization: Proxies can considerably enhance community efficiency by caching often accessed information. This reduces latency and improves response instances, leading to a smoother person expertise. This caching might be notably helpful for apps that often obtain photographs or different massive recordsdata.
- Testing and Debugging: Proxies might be invaluable for testing and debugging Android purposes. They permit builders to simulate numerous community circumstances and take a look at how their apps reply in several conditions. That is essential for guaranteeing dependable efficiency and dealing with community points.
Examples of How Proxies Improve Community Safety and Privateness
Proxies play a essential function in defending delicate info. By routing visitors by a proxy server, apps can encrypt communications and obscure the origin of the request, making it tougher for malicious actors to intercept information.
- Safe Communication Channels: Proxies usually make use of encryption protocols to safeguard information transmitted between the Android app and the server. This safety is especially vital for apps dealing with monetary transactions or private info.
- Information Anonymization: Proxies can masks the person’s IP tackle, successfully hiding their location and on-line exercise. This enhances privateness and permits customers to browse the net or entry particular content material with out revealing their true identification.
Demonstrating The right way to Use a Proxy for Accessing Restricted Content material
Proxies can successfully bypass geographical restrictions and content material filters. They do that by masking the person’s IP tackle, permitting entry to content material not usually out there.
- Bypassing Regional Blocks: By routing visitors by a proxy server positioned in a special area, Android apps can entry content material that is likely to be restricted within the person’s present location. This performance is crucial for creating globally accessible apps.
- Overcoming Content material Filters: Proxies might be employed to avoid content material filters imposed by organizations or governments. That is vital for builders guaranteeing entry to info for customers in numerous areas.
How Proxies Can Be Used for Community Efficiency Optimization
Proxies are worthwhile instruments for optimizing community efficiency. They provide caching capabilities and visitors administration options that enhance response instances.
- Caching Often Accessed Information: Proxies can cache often accessed information, decreasing the necessity for repeated downloads from the unique server. This may drastically enhance the loading velocity of internet pages or different sources inside an app.
- Decreasing Latency: By appearing as an middleman, proxies can cut back the space information has to journey, leading to decrease latency and sooner loading instances. That is notably vital for customers with gradual or unreliable web connections.
Eventualities The place Utilizing a Proxy is Essential for Android Apps
Sure Android apps require the usage of proxies for optimum efficiency and safety. Think about these eventualities:
- World Purposes: Purposes that must be accessible from numerous geographic places often require a proxy to make sure clean performance and content material supply throughout completely different areas.
- Excessive-Visitors Purposes: Apps that deal with a big quantity of person requests profit from proxy caching to enhance response instances and forestall server overload.
Desk Summarizing Use Circumstances for Totally different Proxy Sorts
| Proxy Sort | Use Case |
|---|---|
| HTTP Proxy | Normal internet looking, accessing web sites |
| SOCKS Proxy | Extra superior use circumstances, comparable to tunneling |
| Clear Proxy | Easy redirection, no alteration of person expertise |
| Nameless Proxy | Defending person anonymity, masking IP tackle |
Safety Issues When Utilizing Proxies
Proxies, whereas providing quite a few advantages, introduce a brand new layer of complexity relating to safety. Selecting and configuring a proxy requires cautious consideration of potential vulnerabilities. A poorly secured proxy can compromise your system’s safety and expose delicate information.Understanding the intricacies of proxy safety is essential for sustaining a protected on-line expertise. This part delves into the potential dangers and safeguards related to utilizing proxies, offering a roadmap for safe configuration and choice.
Significance of Safe Proxy Configurations
A safe proxy configuration is paramount to defending your information and privateness. A compromised proxy can turn out to be a gateway for malicious actors to entry your community, doubtlessly stealing delicate info or putting in malware. This makes strong safety measures important for all proxy setups.
Potential Safety Dangers Related to Utilizing Proxies
Proxy servers, although helpful for masking your IP tackle, also can introduce vulnerabilities. Compromised or poorly configured proxies can expose your system to numerous safety dangers, together with:
- Man-in-the-Center Assaults: An attacker positioned between you and the proxy server can intercept and manipulate your communications, doubtlessly stealing credentials or delicate information.
- Malware Infections: If the proxy server is contaminated with malware, your system may turn out to be compromised throughout communication by the proxy.
- Information Breaches: A compromised proxy can lead to an information breach, exposing your private info to unauthorized people.
- Phishing Assaults: A proxy can be utilized to facilitate phishing assaults, the place malicious actors impersonate reputable web sites to deceive customers into revealing delicate info.
- Unencrypted Connections: Utilizing unencrypted proxies for delicate information transmission considerably will increase the danger of interception and information theft.
Measures to Mitigate Safety Threats When Utilizing Proxies
Implementing strong safety measures can considerably mitigate the dangers related to proxy utilization. Think about these important steps:
- Safe Connection Protocols: Make the most of safe protocols like HTTPS to encrypt communication between your system and the proxy server, defending delicate information from interception.
- Robust Authentication: Implement sturdy authentication strategies, like complicated passwords, to stop unauthorized entry to the proxy server.
- Common Safety Audits: Conduct common safety audits of the proxy server to establish and tackle potential vulnerabilities.
- Firewall Safety: Implement a sturdy firewall to dam unauthorized entry makes an attempt to the proxy server.
- Proxy Server Updates: Maintain the proxy server software program up to date with the most recent safety patches to handle recognized vulnerabilities.
Suggestions for Safe Proxy Setup and Configuration
A well-configured proxy is a vital element of a safe on-line expertise. Observe these pointers:
- Confirm Proxy Supplier Repute: Totally analysis and consider the repute of the proxy supplier to make sure their dedication to safety.
- Examine Phrases and Situations: Assessment the phrases and circumstances rigorously to know the supplier’s safety insurance policies and obligations.
- Select a Trusted Supplier: Go for a supplier with a confirmed observe report of safety and a dedication to person privateness.
- Encryption and Authentication: Prioritize proxies that make the most of encryption protocols and strong authentication mechanisms.
- Repeatedly Monitor Proxy Logs: Repeatedly evaluation proxy logs to detect any uncommon exercise or potential safety breaches.
Examples of The right way to Establish a Safe Proxy Supplier
Dependable proxy suppliers usually publish detailed safety info on their web sites. Search for:
- Transparency about safety measures: A supplier that overtly discusses its safety protocols and procedures is an effective signal.
- Constructive opinions and testimonials from different customers: Examine on-line opinions and testimonials from different customers who’ve used the service.
- Trade certifications and compliance: Search for certifications or compliance that validate the supplier’s dedication to safety requirements.
Safety Dangers and Mitigation Methods
| Danger | Mitigation Technique |
|---|---|
| Man-in-the-Center Assaults | Make the most of HTTPS, sturdy authentication, and common safety audits. |
| Malware Infections | Make sure the proxy server is up to date and commonly scanned for malware. |
| Information Breaches | Implement strong safety measures, sturdy authentication, and encryption. |
| Unencrypted Connections | Use encrypted protocols like HTTPS and SSH for delicate information. |
| Phishing Assaults | Be cautious of suspicious hyperlinks and emails relayed by the proxy. |
Superior Proxy Configurations (Non-compulsory)
Diving deeper into proxy configurations unlocks highly effective prospects for tailor-made community entry and enhanced safety. This part explores superior choices, from specialised protocols to customized server setups, equipping you with the instruments to fine-tune your proxy expertise. These superior methods are perfect for customers searching for extra management over their community connections and particular utility wants.Understanding the intricacies of superior proxy configurations empowers you to optimize efficiency, improve safety, and tailor your community expertise to particular purposes or protocols.
This permits for a extra granular management over your community entry, which is particularly worthwhile for builders and customers working with delicate information or purposes requiring particular community settings.
Superior Proxy Protocols
Superior proxy protocols, like SOCKS5, provide larger flexibility and performance in comparison with HTTP proxies. They supply a extra versatile method to community traversal, usually employed in eventualities requiring extra refined management and customization.
- SOCKS5, a robust protocol, permits for authentication, tunnelling, and assist for various community protocols. It is generally used for bypassing firewalls and restrictions, permitting for extra nuanced entry to the web. As an example, a person would possibly use SOCKS5 to entry a restricted web site or service that is blocked by their community’s firewall.
- SOCKS5 is a extra versatile and highly effective different to HTTP proxies, offering larger management and customization choices. It excels in eventualities the place community traversal must be extremely adaptable and versatile.
Customized Proxy Servers
Customized proxy servers grant unparalleled management over community settings. This degree of customization is essential for tailor-made wants and safety protocols.
- Establishing a customized proxy server requires configuring the server software program and establishing the mandatory community connections. That is usually most well-liked by builders or organizations needing fine-tuned management over their proxy configurations.
- Configuring a customized proxy server includes establishing the server software program, comparable to a devoted SOCKS5 proxy server, and configuring community settings to make sure the server is accessible and functioning accurately.
Utility-Particular Proxy Configurations, Setup proxy in android
Sure purposes or companies might require particular proxy settings. Understanding these configurations ensures seamless performance.
- Particular purposes or companies would possibly demand distinctive proxy configurations for correct operation. For instance, a video streaming utility would possibly want a proxy server with explicit bandwidth or latency settings.
- Many purposes, particularly these dealing with multimedia or requiring high-speed connections, profit from having their very own devoted proxy configurations to optimize efficiency and keep a steady connection.
Proxy Authentication Strategies
Varied authentication strategies exist for securing proxy entry.
- Proxy authentication safeguards entry to the proxy server by requiring credentials for authorization. Widespread strategies embrace Primary Authentication, Digest Authentication, and extra specialised varieties.
- Understanding the authentication methodology utilized by the proxy server is crucial to determine a safe connection. Utilizing the right credentials and authentication methodology will guarantee correct entry to the proxy service.
Comparability of Superior Proxy Protocols
A desk summarizing numerous superior proxy protocols and their options is offered under.
| Protocol | Options |
|---|---|
| SOCKS5 | Tunneling, authentication, helps various protocols (HTTP, DNS, and so forth.), enhances safety and suppleness. |
| HTTP Proxy | Easy configuration, usually used for internet looking, appropriate for primary wants. |
| Clear Proxy | Hides the proxy’s identification, usually used for community monitoring. |
Instance Configurations for Totally different Eventualities
Establishing proxies in Android can really feel like navigating a maze, however with the suitable steering, it is surprisingly simple. This part offers concrete examples for numerous proxy setups, from easy configurations to extra complicated eventualities. Understanding these examples will empower you to confidently deal with completely different proxy wants.
Primary HTTP Proxy Configuration
A basic proxy setup makes use of an HTTP proxy server. That is superb for basic internet looking, enabling you to route all of your internet visitors by a chosen server. This usually enhances privateness and safety.
- Community Settings: Entry your Android system’s Wi-Fi settings. Find the choice to configure proxy settings. Enter the proxy server’s IP tackle and port quantity.
- Proxy Server Particulars: For instance, in case your proxy server is positioned at 192.168.1.100 and makes use of port 8080, enter these values within the respective fields.
- Utility-Particular Configurations: Whereas the network-level configuration usually suffices, some apps would possibly require extra proxy settings throughout the utility itself.
Proxy Configuration for a Particular Utility
Typically, you might need to route visitors from a specific app by a proxy. This could possibly be helpful for testing or isolating particular community visitors.
- Establish the App: Decide the appliance for which you want a devoted proxy configuration.
- Examine the App’s Community Settings: Some apps have built-in proxy settings. If out there, modify these settings to specify the proxy server and port.
- Community-Degree Proxy (Various): For apps with out built-in choices, use the network-level proxy settings as described within the Primary HTTP Proxy Configuration, and be certain that the appliance is utilizing the identical proxy server.
Configuring Totally different Proxy Protocols
Proxies assist numerous protocols, together with HTTP, HTTPS, SOCKS4, and SOCKS5. Understanding these distinctions is important for optimum configuration.
- HTTP/HTTPS: Appropriate for basic internet visitors. These protocols are simple to configure.
- SOCKS4/SOCKS5: These are extra versatile, permitting for superior routing and sometimes used for purposes needing greater safety.
- Protocol Choice: Select the protocol that aligns along with your particular wants and utility.
Proxy Configuration for Particular Community Environments
The configuration course of can differ primarily based in your community surroundings, comparable to company networks or academic settings.
- Company Networks: These usually require particular proxy servers and configurations dictated by IT insurance policies.
- Instructional Settings: Much like company environments, colleges usually implement proxy setups for content material filtering and safety.
- Examine with Community Admins: In case your community has pre-defined proxy configurations, contact your community administrator for steering.
Instance Configurations Desk
This desk illustrates completely different use circumstances and their corresponding configurations.
| Use Case | Configuration |
|---|---|
| Normal Internet Shopping | Community-level HTTP proxy configuration with IP tackle and port |
| Particular App Entry | Utility-level proxy configuration (if out there), in any other case network-level proxy |
| Enhanced Safety | SOCKS5 proxy configuration |
| Company Community | Proxy server and port supplied by IT |
