DRM in browser Android units the stage for this enthralling narrative, providing readers a glimpse right into a story that’s wealthy intimately and brimming with originality from the outset. This intricate system, woven into the material of Android net browsers, safeguards the digital rights of copyrighted content material. It ensures that solely approved customers can entry and revel in protected media, like motion pictures and music, performed inside the browser.
Delving deeper, we’ll discover the technical underpinnings of DRM, analyzing its implementation inside Android’s WebView structure. From the safety of content material to the consumer expertise, the multifaceted nature of DRM in Android browsers might be illuminated, revealing the complexities and nuances of this important know-how.
Introduction to DRM in Android Browsers
Digital Rights Administration (DRM) is an important know-how for shielding digital content material on Android units, significantly in terms of net searching. It acts as a gatekeeper, making certain that solely approved customers can entry and revel in content material like motion pictures, music, or premium articles. Consider it as a classy lock system on your digital treasures, stopping unauthorized copying and distribution.DRM in Android browsers performs an important function in safeguarding the monetary pursuits of content material creators and distributors.
By limiting entry to protected content material, DRM helps keep the worth of the content material and permits creators to generate income. This safety mechanism extends to numerous sorts of content material, together with high-definition movies and interactive on-line experiences.
DRM Techniques in Android Browsers, Drm in browser android
Varied DRM techniques are employed in Android browsers to safeguard digital content material. A distinguished instance is Widevine, a extensively used system identified for its capacity to deal with high-quality video playback. This method encrypts video streams, making them inaccessible with out the right decryption keys. Different techniques may be used for several types of content material, corresponding to audio or ebooks, every tailor-made for particular necessities.
Position of DRM in Defending Content material
DRM is crucial for shielding copyrighted materials displayed in Android browsers. By encrypting the content material, DRM makes it unimaginable for unauthorized customers to repeat, distribute, or modify the content material with out the suitable license. This safety extends to a variety of content material, from streaming movies to on-line video games, making certain that content material creators are compensated for his or her work.
Frequent Use Circumstances for DRM in Android Browsers
DRM is employed in a number of widespread eventualities inside Android browsers. Streaming video providers often leverage DRM to stop unauthorized entry to their premium content material. On-line information suppliers use DRM to safeguard articles that require subscriptions. And interactive leisure platforms typically use DRM to guard their video games and experiences.
Totally different DRM Applied sciences and Their Traits
| DRM Know-how | Strengths | Weaknesses |
|---|---|---|
| Widevine | Strong encryption, high-quality video help, widespread adoption | Could be advanced to implement, potential compatibility points with older units |
| PlayReady | Sturdy encryption, extensively used for numerous content material varieties | Much less widespread adoption in comparison with Widevine, might need platform-specific limitations |
| FairPlay | Glorious for securing audio content material, strong safety measures | Primarily centered on audio, won’t be as appropriate for video or advanced interactive content material |
Every DRM know-how is designed to stability safety and value, addressing totally different content material varieties and platform wants. A cautious consideration of those elements is vital for optimum consumer expertise and content material safety.
DRM Implementation in Android WebViews
Android’s WebView, an important element for rendering net content material, typically handles DRM-protected media. This integration ensures safe playback of legally licensed digital content material. The complexity of DRM implementation lies in balancing safety with seamless consumer expertise. It is a delicate dance, requiring cautious coordination between the browser, the DRM module, and the content material supplier.
Structure of Android WebViews and DRM Integration
Android WebViews are layered architectures, with a core rendering engine on the coronary heart. This engine interacts with numerous modules, together with a JavaScript engine, a rendering engine, and finally, a DRM module. The DRM module acts as an middleman, dealing with the cryptographic facets of content material safety. It sits alongside different elements, seamlessly built-in into the WebView’s framework. The particular integration factors and the architectural particulars fluctuate barely throughout totally different variations of Android, making certain compatibility with evolving DRM requirements.
Interactions Between Browser and DRM Parts
The browser, performing because the consumer interface, requests DRM-protected content material from a server. The browser then communicates with the DRM module, offering the required decryption keys and certificates. This communication occurs by well-defined APIs, making certain safe and managed knowledge switch. The DRM module verifies the legitimacy of the request and the content material’s authenticity. As soon as validated, the decryption course of commences.
The interplay is essentially a series of safe calls between the browser, DRM module, and content material supplier.
Content material Decryption and Playback Mechanisms inside WebView
Content material decryption depends on cryptographic algorithms, usually AES or related. The DRM module makes use of these algorithms to decrypt the protected content material. The decrypted knowledge is then handed to the rendering engine, the place it is decoded and exhibited to the consumer. This course of have to be environment friendly to take care of a easy playback expertise. A strong caching mechanism for decryption keys helps to hurry up subsequent performs of the identical content material.
Steps in DRM-Protected Content material Loading and Playback
- The consumer initiates playback of DRM-protected content material. The browser sends a request to the server for the protected media.
- The server delivers the encrypted content material together with crucial DRM data (e.g., licenses, keys).
- The browser communicates with the DRM module, offering the obtained knowledge.
- The DRM module validates the content material and acquires the decryption keys, both from the server or from an area cache.
- The decrypted content material is then despatched to the rendering engine for playback.
- If the license expires or is revoked, the playback halts, prompting the consumer to amass a brand new license.
Stream of Information Between Parts
| Part | Motion | Information Stream |
|---|---|---|
| Browser | Requests protected content material | Request to server |
| Server | Delivers encrypted content material and DRM data | Encrypted content material, license to browser |
| Browser | Passes content material to DRM module | Encrypted content material to DRM |
| DRM Module | Validates content material and obtains decryption keys | Decryption keys to browser |
| Browser | Passes decrypted content material to renderer | Decrypted content material to renderer |
| Renderer | Shows the content material | Content material to show |
DRM Safety Issues in Android Browsers
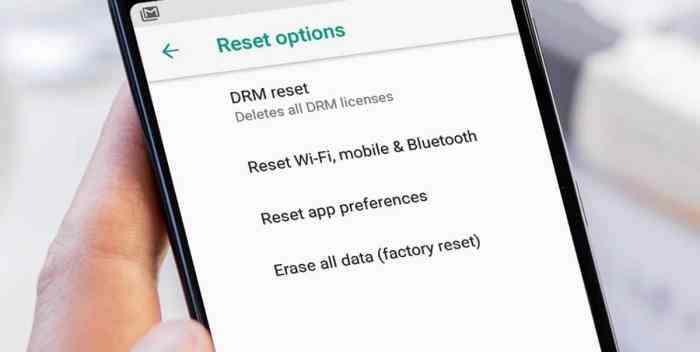
Defending digital content material in browsers is an important activity, particularly when coping with DRM-protected materials. Strong safety measures are paramount to stop unauthorized entry and guarantee honest use. This part explores the vulnerabilities in DRM implementations inside Android browsers, potential exploits, and the very important function of safety protocols.The implementation of Digital Rights Administration (DRM) in Android browsers, whereas essential for copyright safety, additionally introduces potential safety weaknesses.
These weaknesses can come up from vulnerabilities within the DRM techniques themselves, the Android working system, and even the browser’s implementation of the DRM APIs. Understanding these vulnerabilities is crucial to mitigating dangers.
Safety Vulnerabilities in DRM Implementations
Weaknesses in DRM implementations can stem from numerous sources. These vulnerabilities could also be associated to flaws within the DRM system’s design, coding errors within the implementation, and even weaknesses within the underlying cryptographic algorithms. Incorrect implementation of safety protocols can expose DRM-protected content material to unauthorized entry, circumvention, or piracy. Attackers might exploit these weaknesses to entry or modify the content material, bypassing the meant utilization rights.
Potential Assault Vectors and Exploit Situations
Varied assault vectors can goal DRM-protected content material in Android browsers. One widespread assault is thru exploiting vulnerabilities within the DRM middleware. A second methodology is focusing on flaws within the Android OS’s safety mechanisms that work together with the DRM APIs. Attackers might attempt to bypass or manipulate the DRM authentication course of or the content material decryption course of to achieve unauthorized entry.
For example, subtle attackers may develop exploits that use vulnerabilities within the browser’s DRM dealing with to bypass safety controls and achieve entry to protected content material.
Significance of Safety Protocols in DRM Techniques
Strong safety protocols are important to make sure the integrity and confidentiality of DRM-protected content material. These protocols ought to contain robust encryption algorithms, safe key administration, and rigorous entry management mechanisms. Using established safety requirements and practices is important for DRM techniques. Safety protocols needs to be commonly audited and up to date to handle rising threats.
Greatest Practices for Securing DRM Implementations
A number of greatest practices can improve the safety of DRM implementations in Android browsers. Rigorous code opinions, penetration testing, and safety audits are essential to detect and repair vulnerabilities early within the growth cycle. Utilizing robust cryptographic algorithms and adhering to industry-standard safety protocols can considerably bolster safety. Using safe key administration methods is important.
Comparability of Safety Measures for DRM Safety
| Safety Measure | Description | Effectiveness |
|---|---|---|
| Sturdy Encryption Algorithms | Utilizing strong encryption strategies to guard content material | Excessive |
| Safe Key Administration | Implementing safe storage and dealing with of cryptographic keys | Excessive |
| Common Safety Audits | Conducting common audits to establish and repair vulnerabilities | Medium to Excessive |
| Entry Management Mechanisms | Implementing strict entry controls to restrict content material entry | Excessive |
| Penetration Testing | Simulating real-world assaults to search out vulnerabilities | Excessive |
Person Expertise and DRM in Android Browsers

DRM, or Digital Rights Administration, is an important know-how for shielding digital content material. Nonetheless, its implementation in Android browsers can considerably affect the consumer expertise. This part delves into the advanced relationship between DRM and consumer expertise, highlighting each challenges and potential options.DRM’s affect on consumer expertise is multifaceted. From loading instances to accessibility and engagement, the implementation of DRM can both improve or detract from the general searching expertise.
Understanding these nuances is essential to constructing strong and user-friendly Android browsers.
Impression on Loading Occasions and Playback High quality
DRM typically introduces overhead, probably slowing down content material loading instances. Encryption and decryption processes inherent in DRM can improve latency, impacting the general responsiveness of the browser. Furthermore, the standard of playback will also be affected. If the DRM system is not optimized, it’d introduce artifacts or glitches, particularly throughout transitions or fast-paced scenes, negatively impacting the viewing expertise.
Totally different DRM techniques have various ranges of effectivity, affecting loading speeds and the standard of playback. Cautious optimization is required to attenuate the affect on the consumer expertise.
Impression on Content material Accessibility
DRM can current challenges for customers with disabilities. For example, customers who depend on display screen readers may encounter difficulties accessing and navigating DRM-protected content material. Moreover, captions and subtitles may be affected by DRM restrictions, making content material inaccessible to customers who depend on these options. Accessibility concerns have to be factored into the DRM implementation course of.
Impression on Person Engagement with Internet Content material
DRM’s affect extends past loading instances and accessibility. The perceived limitations imposed by DRM can deter consumer engagement with net content material. If customers understand a big delay or degradation in high quality as a result of DRM, they may be much less prone to work together with the protected content material, impacting consumer satisfaction and engagement charges. This may result in a big decline in content material consumption.
Strategies for Optimizing Person Expertise Whereas Sustaining DRM Safety
A number of methods can optimize consumer expertise whereas making certain DRM safety. Environment friendly DRM implementations decrease latency and processing overhead. This may be achieved by optimized algorithms and {hardware} acceleration. Correct configuration and cautious tuning of the DRM system can drastically enhance loading instances. Moreover, making certain compatibility with numerous DRM requirements and supporting totally different playback units is vital for a optimistic consumer expertise.
Desk Contrasting Totally different Person Experiences Associated to DRM-Protected Content material
| DRM Implementation | Loading Time | Playback High quality | Accessibility | Person Engagement |
|---|---|---|---|---|
| Optimized DRM | Quick | Excessive | Glorious | Excessive |
| Inefficient DRM | Gradual | Low | Poor | Low |
| Legacy DRM | Variable | Variable | Variable | Variable |
DRM Compatibility and Interoperability
Digital Rights Administration (DRM) techniques, whereas essential for content material safety, typically face challenges in seamless operation throughout totally different Android browser variations and units. This necessitates cautious consideration of compatibility and interoperability to make sure a easy consumer expertise. Understanding these intricacies is essential to delivering a dependable and constant platform for protected content material.Totally different DRM implementations can considerably have an effect on consumer expertise.
Compatibility points typically manifest as playback failures, restricted content material availability, or irritating error messages. Addressing these hurdles is crucial for sustaining a optimistic consumer notion and inspiring widespread adoption of DRM-protected content material.
Compatibility of Varied DRM Techniques with Android Browser Variations
Totally different DRM techniques have various levels of compatibility with totally different Android browser variations. This stems from the dynamic nature of software program updates and the evolving specs of DRM implementations. Early variations of Android won’t help newer DRM requirements, resulting in incompatibility. Conversely, newer browser variations might battle with older DRM applied sciences.
Frequent Compatibility Points
A variety of compatibility points can come up. These embrace:
- Inconsistent Playback: Some DRM implementations may result in inconsistent playback throughout totally different Android browser variations. This might contain buffering points, playback errors, or the lack to play content material in any respect. This typically arises as a result of differing interpretations of the DRM specs.
- Restricted Content material Availability: Particular DRM implementations may prohibit entry to sure content material varieties or sources on sure Android browser variations. This may be as a result of licensing limitations or variations in the way in which the DRM handles numerous media codecs.
- Safety Vulnerabilities: Older or much less strong DRM implementations may have safety vulnerabilities which are exploited by malicious actors. This may compromise the integrity of protected content material and result in unauthorized entry.
Interoperability Challenges Between Totally different DRM Techniques and Android Variations
Interoperability challenges typically come up from the intricate nature of various DRM techniques. Totally different DRM techniques might make use of numerous encoding schemes, encryption algorithms, and entry management mechanisms. This may create hurdles within the seamless integration of content material throughout totally different platforms. For example, a DRM system designed for a particular working system won’t work seamlessly with a special working system or model of a browser, even when the underlying know-how is analogous.
Impression of Totally different DRM Implementations on Person Expertise Throughout Gadgets
Totally different DRM implementations can have important results on the consumer expertise throughout numerous units. For instance, a specific DRM system may carry out properly on high-end units however encounter efficiency points on lower-end units. This disparity can have an effect on the general consumer satisfaction and result in frustration for these utilizing much less highly effective units. Furthermore, the way in which DRM handles content material licensing and utilization restrictions can have an effect on consumer expertise in a wide range of methods.
Compatibility Matrix for DRM Techniques and Android Browser Variations
An in depth compatibility matrix could be invaluable. Such a desk would supply a transparent overview of the compatibility between totally different DRM techniques and numerous Android browser variations. It might facilitate fast identification of potential compatibility points and information builders in deciding on applicable DRM implementations.
| DRM System | Android Browser Model 10 | Android Browser Model 11 | Android Browser Model 12 |
|---|---|---|---|
| DRM A | Appropriate | Appropriate | Incompatible |
| DRM B | Incompatible | Appropriate | Appropriate |
| DRM C | Appropriate | Incompatible | Appropriate |
This desk supplies a simplified instance. A complete matrix would come with extra DRM techniques and a broader vary of Android browser variations.
DRM and Privateness Issues

Defending your digital content material is vital, however so is your privateness. Digital Rights Administration (DRM) techniques, whereas designed to safeguard content material, can elevate privateness considerations if not carried out rigorously. Understanding these considerations is essential for making certain a safe and reliable digital expertise.DRM techniques, of their quest to stop unauthorized copying, generally acquire consumer knowledge. This knowledge can vary from fundamental searching habits to extra delicate data, relying on the system’s design and implementation.
This knowledge assortment can affect your privateness.
Privateness Implications of DRM
DRM techniques, by their nature, typically want to trace consumer exercise to implement entry restrictions. This monitoring can embrace monitoring playback instances, gadget identification, and even location knowledge in sure eventualities. Customers want to concentrate on these implications and select techniques that stability content material safety with privateness. A consumer’s searching habits, together with the content material they entry, may be recorded.
Information Assortment Practices
Totally different DRM techniques make use of numerous strategies for accumulating consumer knowledge. Some might log each interplay with protected content material, together with the length of viewing or listening. Others may acquire gadget data, such because the distinctive identifiers of your cellular gadget. This knowledge assortment can vary from innocuous particulars just like the gadget’s working system model to extra probably delicate data. It is essential to grasp the particular knowledge assortment practices of every DRM system you employ.
Potential Information Breaches
A possible vulnerability of DRM techniques is the chance of knowledge breaches. If a DRM supplier experiences a safety breach, the collected consumer knowledge could possibly be compromised, resulting in potential misuse or unauthorized entry to private data. Actual-world examples of knowledge breaches affecting different techniques present how vital strong safety measures are. Defending consumer knowledge is paramount within the digital age.
Mitigating Privateness Dangers
A number of measures can assist mitigate the potential privateness dangers related to DRM techniques. Firstly, customers ought to rigorously assessment the privateness insurance policies of the DRM suppliers they select. Techniques with clear and complete privateness insurance policies are preferable. Secondly, using robust passwords and two-factor authentication for DRM accounts can considerably improve safety. Moreover, enabling encryption on units and networks is crucial to guard knowledge transmission.
Lastly, holding DRM software program up to date with the newest safety patches is essential to safeguard in opposition to identified vulnerabilities.
Evaluating DRM Supplier Privateness Insurance policies
| DRM Supplier | Privateness Coverage Transparency | Information Assortment Practices | Safety Measures |
|---|---|---|---|
| Supplier A | Clear and concise; Artikels knowledge collected and the way it’s used. | Restricted knowledge assortment; primarily centered on entry management. | Strong safety measures; common safety audits. |
| Supplier B | Obscure and unclear; inadequate particulars on knowledge dealing with. | In depth knowledge assortment; monitoring searching habits, gadget particulars, and extra. | Common safety measures; no clear data on audit processes. |
| Supplier C | Complete and express; consists of detailed explanations. | Restricted knowledge assortment; focuses on important data. | Sturdy safety measures; emphasis on consumer knowledge safety. |
This desk presents a simplified comparability; thorough analysis and understanding of every supplier’s particular coverage are important. All the time learn and perceive the privateness coverage earlier than utilizing any DRM service.
Future Traits in DRM for Android Browsers: Drm In Browser Android
The digital realm is consistently evolving, and DRM techniques, essential for safeguarding copyrighted content material, should adapt. Android browsers, on the forefront of this digital panorama, are poised to witness important developments in DRM know-how, impacting each customers and content material creators. This transformation guarantees a safer and complicated expertise for everybody.Rising applied sciences, from enhanced encryption strategies to blockchain-based options, are reshaping the way in which we shield digital belongings.
This evolution in DRM is vital to sustaining the integrity of on-line content material and fostering a thriving digital ecosystem.
Rising DRM Applied sciences
Trendy DRM techniques are shifting past easy copy safety in direction of a extra complete method that encompasses consumer rights administration, authentication, and verifiable provenance. This shift is pushed by the growing sophistication of digital content material creation and consumption. Key developments embrace the event of extra strong encryption algorithms, the mixing of blockchain know-how for safe content material monitoring and verification, and the emergence of recent hardware-based safety options.
These developments are essential for sustaining the integrity of on-line content material.
Potential Improvements and Developments
A number of improvements are shaping the way forward for DRM. These embrace improved consumer interfaces that provide extra granular management over content material entry and utilization rights, together with enhanced help for numerous content material codecs. Moreover, the event of adaptive DRM options, which modify to totally different units and community situations, might be essential for optimum consumer experiences. Contemplate the streaming of high-definition video on a tool with restricted bandwidth; adaptive DRM options can intelligently handle the standard of the stream to take care of a easy viewing expertise.
Impression on Android Browsers
The affect of those developments on Android browsers might be profound. Improved security measures, like enhanced encryption, will shield customers from unauthorized entry to content material. The mixing of blockchain know-how will guarantee higher transparency and authenticity in content material distribution, whereas adaptive DRM options will ship a constant and high-quality expertise throughout numerous units and community situations. Customers will profit from enhanced management over their content material entry and utilization rights.
Future Instructions of DRM
The way forward for DRM is prone to transfer towards a extra decentralized and user-centric mannequin. This implies higher emphasis on consumer selection and management over their digital content material, with a diminished reliance on centralized servers for content material administration. Consider a system the place customers personal their digital content material and may simply share it with others inside the bounds of their rights, utilizing strong digital rights administration techniques.
This shift will result in a extra dynamic and modern digital ecosystem.
Potential Challenges and Alternatives
The evolution of DRM presents each challenges and alternatives. One problem lies in sustaining compatibility throughout numerous units and working techniques. Guaranteeing interoperability between totally different DRM techniques might be vital for seamless content material entry. A key alternative is the potential to create extra participating and user-friendly content material entry experiences. This may contain incorporating DRM functionalities into purposes in a means that enhances the consumer expertise, fairly than making a barrier to entry.
Moreover, fostering belief and transparency in content material distribution might be essential for constructing a sustainable digital ecosystem.
- Compatibility Points: Guaranteeing seamless content material entry throughout numerous units and working techniques might be essential. This consists of contemplating the various {hardware} and software program configurations that Android customers make use of. Addressing this problem head-on might be vital to attaining a really common expertise for customers.
- Person Expertise: DRM needs to be built-in seamlessly into the consumer expertise. This implies minimizing the friction customers expertise when accessing content material protected by DRM. A user-friendly expertise is paramount to attaining widespread adoption and optimistic suggestions from customers.
- Privateness Issues: Balancing DRM safety with consumer privateness might be a vital side of future growth. Sustaining consumer privateness with out compromising content material safety would require cautious consideration of knowledge dealing with and utilization practices.
