Mac deal with android cellphone, a seemingly easy idea, really holds a wealth of details about how your system interacts with the digital world. Understanding this distinctive identifier is vital to comprehending your cellphone’s networking habits and safety implications. This exploration delves into the position of the MAC deal with inside the Android ecosystem, analyzing its functionalities, implications, and the essential position it performs in your cellphone’s connectivity.
Android telephones use varied strategies to determine themselves, and the MAC deal with is a basic element on this course of. It is a distinctive {hardware} deal with assigned to your cellphone’s community interface, performing as its digital fingerprint. We’ll discover how this deal with is used, managed, and the way it influences your cellphone’s potential to hook up with and talk on networks.
Understanding Android Machine Identification
Android gadgets, like tiny digital personas, want distinctive identifiers to work together with the huge community. This identification course of ensures clean communication and information integrity. Understanding how these gadgets determine themselves is essential for varied functions, from seamless app interactions to safe community entry.Android makes use of a mixture of {hardware} and software program components to uniquely determine every system. These strategies, whereas distinct, work collectively to supply a sturdy and dependable identification system.
Strategies of Android Machine Identification
Android employs quite a lot of strategies to tell apart one system from one other. These methods guarantee every cellphone retains its individuality, enabling correct record-keeping and environment friendly communication inside the ecosystem.
- {Hardware}-based identifiers are basic to Android’s identification technique. These identifiers are embedded inside the system itself, making them persistent and dependable.
- Software program-based identifiers are dynamic, adapting to the system’s atmosphere. These identifiers typically contain facets just like the system’s working system model, put in functions, and different software program traits.
The Function of the MAC Deal with
The Media Entry Management (MAC) deal with is a vital hardware-based identifier. It serves as a singular serial quantity for the system’s community interface card (NIC). This deal with is essential for community communication, enabling the system to speak and join with different gadgets on the community.
- The MAC deal with is a vital a part of community communication. It permits gadgets to be acknowledged on the community, facilitating seamless information transmission.
- The MAC deal with, being a {hardware} identifier, stays fixed all through the system’s lifecycle. This makes it a dependable technique to monitor and determine the system no matter software program modifications or modifications.
Relationship Between MAC Deal with and Android OS
The Android working system leverages the MAC deal with to facilitate community connections. The OS interacts with the {hardware} to make the most of the MAC deal with for communication functions.
- The Android OS makes use of the MAC deal with for community operations, making certain clean information transmission between gadgets.
- The OS would not instantly handle or modify the MAC deal with. It acts as an middleman, utilizing the deal with for community capabilities.
Elements Concerned in Android Machine Identification
The desk under Artikels the important thing parts concerned within the means of figuring out an Android system. Every element performs a definite position within the intricate dance of system recognition.
| Part | Description | Operate | Instance |
|---|---|---|---|
| MAC Deal with | A novel hexadecimal deal with assigned to a community interface card (NIC). | Identifies the system’s community interface for communication. | 00:1A:2B:3C:4D:5E |
| Android Model | The particular model of the Android working system put in on the system. | Differentiates gadgets based mostly on OS model. | Android 13 |
| IMEI (Worldwide Cellular Gear Id) | A novel 15-digit quantity assigned to a cellular system. | Identifies the cellular system in a mobile community. | 35987654321098765 |
| Serial Quantity | A novel alphanumeric string assigned to the system throughout manufacturing. | Identifies the particular system occasion. | SN1234567890ABCDEF |
MAC Deal with Performance on Android
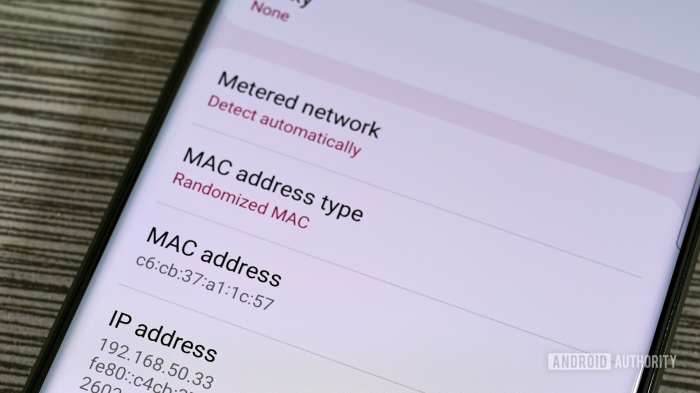
Android telephones, like miniature digital universes, make the most of a singular identifier for seamless community interactions. This identifier, the Media Entry Management (MAC) deal with, performs a pivotal position in enabling communication and configuration inside the Android ecosystem. Understanding its performance is essential for greedy how your cellphone connects to the world.The MAC deal with, a hard and fast {hardware} identifier, acts as a singular deal with to your cellphone’s community interface card (NIC).
Consider it as your cellphone’s private license plate on the community freeway. It permits gadgets to tell apart between one another, enabling focused information transmission and reception. This basic position extends to numerous communication processes inside the Android OS.
MAC Deal with in Community Communication
The MAC deal with is the cornerstone of native space community (LAN) communication. It permits gadgets to determine one another instantly on the identical community. Information packets, the basic models of community communication, are addressed utilizing MAC addresses. This ensures that information reaches the meant recipient. As an illustration, if you ship a message via a Wi-Fi community, your cellphone makes use of its MAC deal with to focus on the message to the right recipient.
MAC Deal with Administration inside Android
Android meticulously manages the MAC deal with to make sure clean communication. The working system interacts with the {hardware} to keep up and make the most of the deal with. This intricate course of, invisible to the consumer, ensures dependable community connections. The Android OS additionally offers mechanisms for altering or buying a MAC deal with, however that is usually executed via complicated interactions with the community stack and shouldn’t be tried by common customers.
Use of MAC Deal with in Community Configurations
Community configurations typically leverage MAC addresses for particular functions. As an illustration, in a wi-fi community, MAC addresses are used to filter which gadgets are allowed entry. This safety function restricts unauthorized entry and ensures that solely permitted gadgets can hook up with the community.
Illustrative Communication Flowchart
+-----------------+ +-----------------+
| Machine A (MAC) |----->| Machine B (MAC) |
+-----------------+ +-----------------+
| Community Request | | Community Response |
| (Supply MAC, Dest) | | (Supply MAC, Dest) |
+-----------------+ +-----------------+
| | | |
| | | |
+-----------------+ +-----------------+
|Community Interface Card|
| (Handles MAC) |
+---------------------+
This flowchart depicts a fundamental communication course of.
Machine A initiates a request to Machine B. The request contains each the supply and vacation spot MAC addresses. The community interface card (NIC) of Machine A makes use of the MAC deal with to ship the request to the suitable community. Machine B’s NIC, in flip, makes use of the vacation spot MAC deal with to obtain the request and course of it.
Implications of MAC Addresses in Android
Android, like many different working programs, makes use of MAC addresses for system identification. Whereas seemingly innocuous, this observe presents safety implications which can be essential to know. A deeper dive into how MAC addresses are used and misused on Android is important for anybody involved about their system’s safety.
Understanding the nuances of MAC deal with utilization is significant for navigating the complexities of cellular safety. Understanding how Android handles MAC addresses, each in regular operation and beneath potential risk, is paramount to safeguarding your information. Android’s dealing with of MAC addresses, whereas usually safe, shouldn’t be impervious to assault, and understanding the potential vulnerabilities is vital.
Safety Implications of MAC Addresses
MAC addresses, distinctive identifiers for community interfaces, are doubtlessly susceptible to exploitation. They can be utilized to trace gadgets throughout networks, doubtlessly resulting in privateness breaches. Moreover, malicious actors may use MAC deal with manipulation to bypass safety measures or impersonate reliable gadgets. This can be a important concern for Android customers.
MAC Deal with Manipulation and Malicious Use
A typical malicious use of MAC addresses is spoofing. Attackers can manipulate the MAC deal with of their system to look as one other, reliable system on a community. This permits them to doubtlessly achieve unauthorized entry to assets or bypass safety measures. One other potential risk is the usage of MAC deal with filtering to dam reliable gadgets. Malicious actors may doubtlessly use this to dam licensed entry to particular gadgets.
Dealing with MAC Addresses in Android Safety Contexts
Android’s safety framework incorporates MAC deal with dealing with inside its total safety technique. Completely different safety contexts, comparable to Wi-Fi connections and Bluetooth interactions, deal with MAC addresses in distinctive methods. As an illustration, Wi-Fi entry factors usually use MAC deal with filtering for safety, whereas Android’s Bluetooth implementation contains protocols for safe system pairing.
Comparability with Different Identification Strategies
In comparison with different system identification strategies, MAC addresses current particular safety considerations. Distinctive system identifiers (UDIDs) or IMEI numbers, whereas additionally used for identification, typically present extra granular management over entry and safety. Nevertheless, they don’t seem to be with out their very own potential vulnerabilities. Understanding the trade-offs between totally different identification strategies is crucial for knowledgeable safety selections. The implications of utilizing MAC addresses have to be thought of along side different safety measures.
This multifaceted strategy is essential for sustaining a powerful safety posture.
MAC Deal with and Community Connectivity: Mac Deal with Android Telephone

Your Android cellphone’s MAC deal with is like its distinctive social safety quantity on the community. It is essential for figuring out the system and enabling seamless communication with different gadgets and community infrastructure. Understanding how this deal with capabilities inside the community is vital to troubleshooting potential connectivity issues.
How MAC Addresses Have an effect on Community Connectivity
The MAC deal with performs a basic position in establishing and sustaining community connections on Android. It is utilized by the system’s community interface card (NIC) to determine itself to different gadgets on the identical native community. This distinctive identifier ensures that information packets are appropriately routed to the meant recipient. With out a correct MAC deal with, information transmission could be chaotic, with packets going to the fallacious locations.
Consider it like attempting to ship a letter with no right deal with – it would not arrive at its meant vacation spot.
Function of MAC Deal with in Establishing and Sustaining Connections
The MAC deal with is intrinsically linked to the method of community connection institution. When your Android cellphone makes an attempt to hook up with a Wi-Fi community, its MAC deal with is included within the connection request. The entry level (router) then verifies this deal with in opposition to its database, confirming the system’s authorization. Sustaining a steady connection depends on the constant recognition and verification of this deal with.
The MAC deal with primarily serves as a digital passport to your cellphone on the community, making certain licensed entry and information circulation.
Community Protocols Counting on MAC Addresses
A number of community protocols instantly leverage the MAC deal with for efficient information transmission. These protocols make sure that information is delivered effectively and reliably throughout the community.
| Protocol | Description | Function | Instance |
|---|---|---|---|
| Media Entry Management (MAC) | Defines how gadgets on a community share the transmission medium | Basic protocol; controls entry to the shared community | Handles the precise transmission of knowledge frames between gadgets |
| IP (Web Protocol) | Handles routing information packets throughout networks | Larger-level protocol that makes use of MAC addresses to ship information to the right system on an area community | Your cellphone sends an IP packet to a server; the router makes use of the MAC deal with to ahead the packet to the right system |
| ARP (Deal with Decision Protocol) | Maps IP addresses to MAC addresses | Important for translating IP addresses to MAC addresses, permitting the system to search out the right recipient | When your cellphone needs to ship information to a different system, it makes use of ARP to search out the corresponding MAC deal with. |
| 802.11 (Wi-Fi) | Specifies the requirements for wi-fi native space networks (WLANs) | Gives the framework for wi-fi communication; makes use of MAC addresses for system identification | Your Android cellphone connects to a Wi-Fi community utilizing the 802.11 customary and its MAC deal with. |
Troubleshooting Community Connectivity Points Associated to MAC Deal with
In case you encounter community connectivity issues, analyzing the MAC deal with can typically pinpoint the problem. Confirm that the MAC deal with is appropriately configured in your Android system. Examine if the Wi-Fi community you are attempting to hook up with has restrictions on the allowed MAC addresses. Moreover, guarantee your system’s MAC deal with hasn’t been modified or blocked by the community administrator.
Contact your web service supplier or community administrator if you happen to suspect a broader concern with the community configuration.
MAC Deal with and Privateness Issues

Within the digital age, our on-line actions depart a path, and understanding how this information is dealt with is essential. MAC addresses, whereas important for community communication, additionally elevate privateness considerations. This part delves into the potential dangers and the way Android addresses them.
Privateness Implications of MAC Addresses
MAC addresses, distinctive identifiers for community gadgets, may be doubtlessly linked to consumer location and exercise patterns. This may elevate important privateness considerations, significantly if not dealt with responsibly. Cautious consideration is important to stability the sensible use of MAC addresses with consumer rights.
Monitoring Consumer Location and Actions
Malicious actors or organizations may doubtlessly leverage MAC addresses to trace consumer motion throughout totally different networks. That is doable if MAC addresses are persistently logged and correlated with different information factors, comparable to Wi-Fi entry factors and mobile towers. A consumer connecting to a public Wi-Fi hotspot in a shopping center could possibly be doubtlessly tracked in that location if the community operator logs MAC addresses.
Figuring out Gadgets, Mac deal with android cellphone
MAC addresses are inherently identifiers, and their use can allow the identification of particular gadgets. This functionality may be leveraged for varied functions, each reliable and doubtlessly malicious. For instance, a tool utilizing a selected MAC deal with is likely to be flagged as a part of a community safety system or by a service supplier. Nevertheless, this is also exploited for malicious functions.
Android’s Method to Consumer Privateness
Android, in its design, prioritizes consumer privateness. It employs a mixture of mechanisms to mitigate the potential dangers related to MAC addresses. Android’s strategy displays a dedication to safeguarding consumer information.
Mitigating Privateness Issues
Android’s strategy to mitigating privateness considerations contains the cautious dealing with of MAC addresses. The OS would not all the time use the MAC deal with instantly for identification. As a substitute, it typically depends on different, extra anonymized identifiers or community data.
Moreover, Android encourages community suppliers to undertake privacy-respecting practices. That is vital in minimizing the potential for MAC addresses getting used to trace consumer exercise. By following greatest practices, the danger of misuse may be considerably decreased.
In abstract, whereas MAC addresses are a basic element of community communication, Android’s design issues and greatest practices goal to guard consumer privateness. This stability between performance and consumer rights is essential within the digital panorama.
Alternate options and Future Traits
Android gadgets, like all know-how, are consistently evolving. The way in which we determine them can also be altering, shifting past the normal reliance on MAC addresses. This shift displays a broader development in direction of safer and privacy-conscious approaches to system identification. The long run holds thrilling potentialities for a way we’ll acknowledge and work together with these highly effective cellular instruments.The standard use of MAC addresses for system identification, whereas easy, presents sure limitations, particularly within the realm of privateness and safety.
Alternate options are rising that supply benefits in these areas. These strategies goal to stability the necessity for identification with the rising considerations about consumer privateness.
Different Strategies for Machine Identification
Understanding the constraints of MAC addresses is vital to exploring various strategies. A variety of methods are being explored, every with its personal set of strengths and weaknesses. These alternate options typically deal with extra summary and fewer instantly traceable traits.
- Machine fingerprints: This system leverages varied system traits, comparable to {hardware} configurations, software program variations, and put in apps, to create a singular identifier. The fingerprint is a composite of those components, making it extra complicated and fewer instantly tied to bodily {hardware}, like a MAC deal with. This makes it extra resilient to spoofing.
- Telephony identifiers: These identifiers, like IMEI and MEID, are linked to the cellphone’s mobile community identification. They’re used for mobile communications and may be employed for system identification. Nevertheless, their reliance on the mobile community means they may not be accessible in all situations, comparable to when utilizing Wi-Fi.
- Machine IDs from different companies: Varied companies, like working system software program updates and app shops, can present distinctive system identifiers. These IDs is likely to be tied to consumer accounts or system registration, including one other layer of identification, typically mixed with fingerprints or telephony identifiers.
- Hybrid approaches: Many present programs are shifting in direction of a mixture of those methods. Combining a number of identifiers can improve accuracy and cut back reliance on a single, doubtlessly susceptible methodology. This strategy permits for extra dependable system identification whereas minimizing the dangers related to counting on a single methodology.
Benefits and Disadvantages of Alternate options
A vital facet of any various identification methodology is its benefits and drawbacks compared to the usage of MAC addresses.
| Technique | Benefits | Disadvantages |
|---|---|---|
| Machine Fingerprints | Stronger privateness, much less reliance on bodily {hardware} | Complexity in implementation, potential for false positives |
| Telephony Identifiers | Established framework, tied to mobile community | Restricted availability in Wi-Fi environments, potential for misuse by carriers |
| Machine IDs from different companies | Broadly accessible, typically built-in into present programs | Potential privateness considerations associated to information assortment and utilization by third events |
| Hybrid Approaches | Elevated accuracy and resilience, decreased reliance on a single methodology | Complexity in implementation, potential for elevated information assortment |
Future Traits in Android Machine Identification
The way forward for system identification in Android is evolving quickly. The development is in direction of a extra nuanced and complete strategy, combining totally different strategies.
Potential Modifications within the Use of MAC Addresses
The position of MAC addresses in Android system identification is prone to diminish over time. The rising emphasis on privateness and safety is pushing in direction of extra summary and fewer instantly traceable strategies.
Rising Applied sciences
Rising applied sciences like superior cryptographic methods and safe, decentralized identification programs will seemingly play a bigger position in system identification sooner or later. These applied sciences goal to stability safety and privateness.
